We are told that the flag is the email of the admin account. Upon arriving at the site, I am greeted with this rather unpleasant photo:
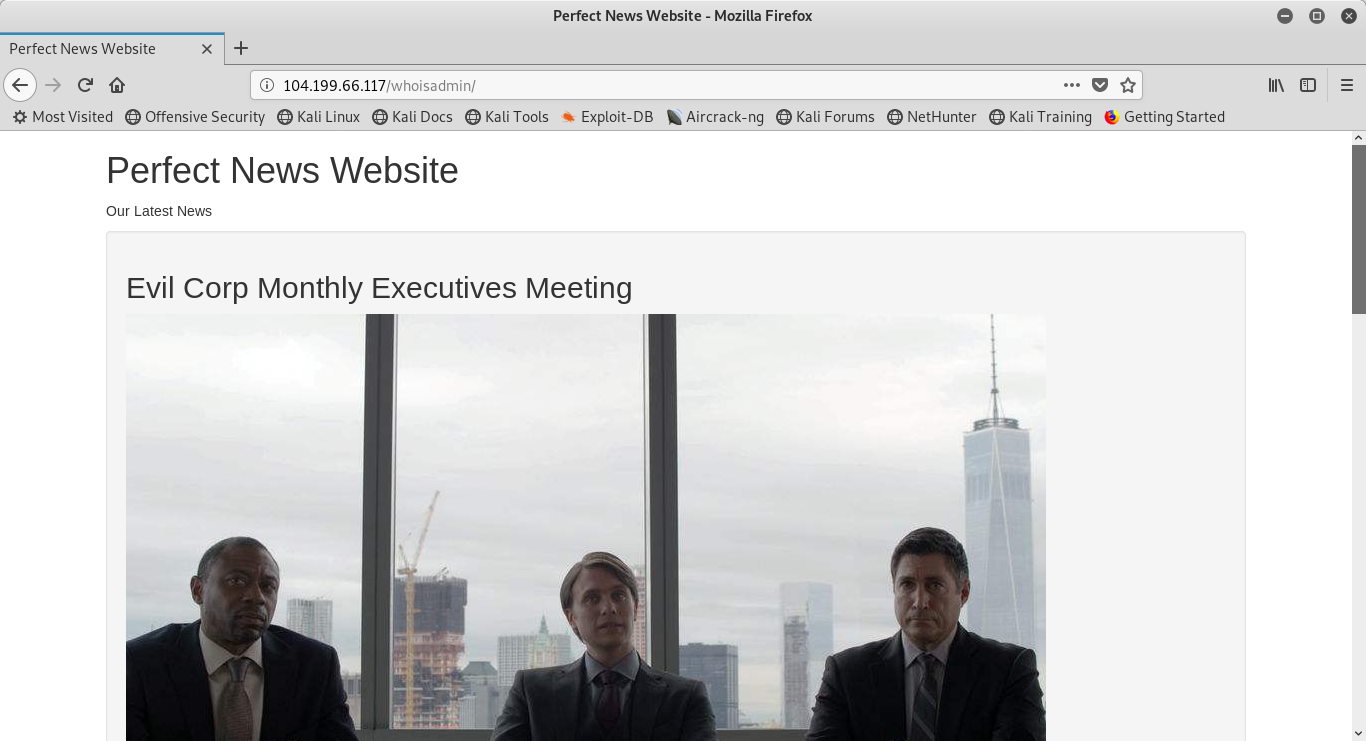
In this instance, I notice that there are many photos and embedded links in the page. Clicking on a few of these links leads me to noting something interesting in the url. Observe what happens when I click on the second article in the page:
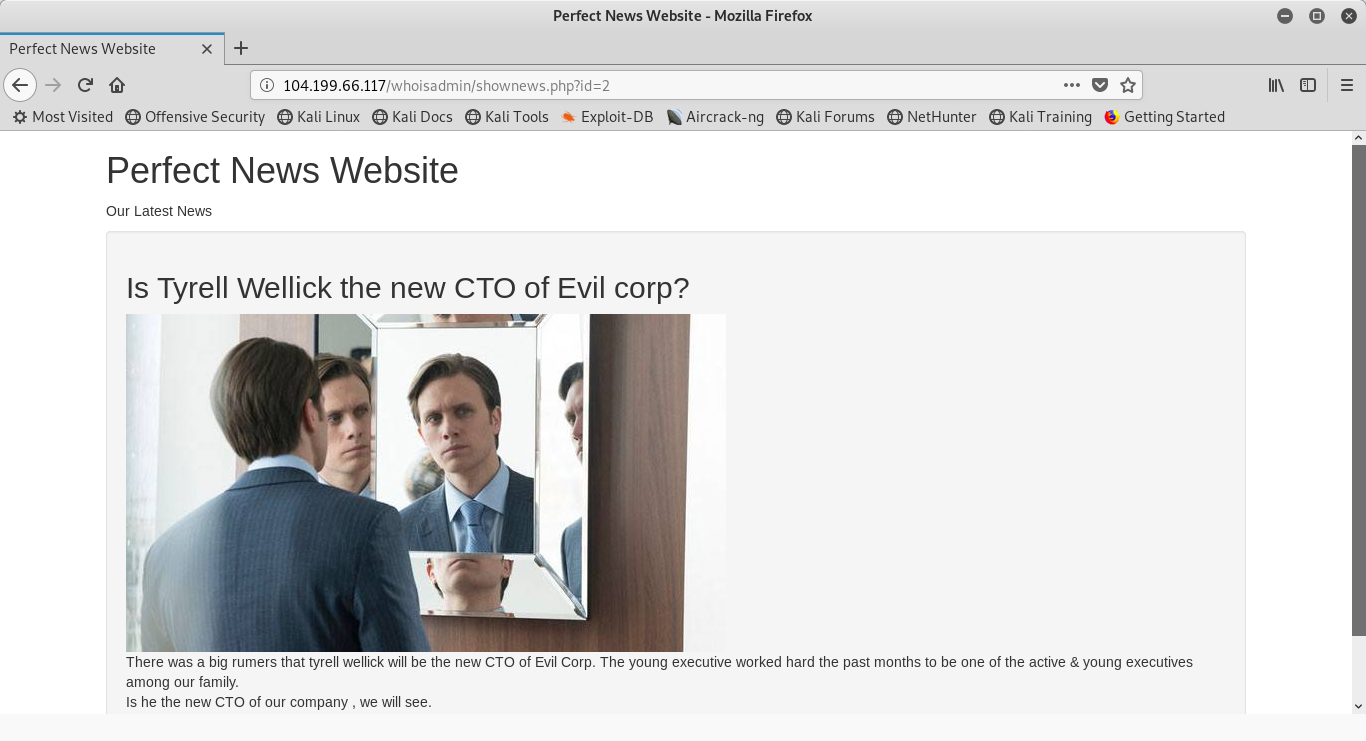
I have no discovered that there is a url variable that is being displayed. My first inclination is to test for SQL injection based on if Web Parameter Tampering is possible. Of course, the best way to test for this is with a single ‘. Consider the following output:
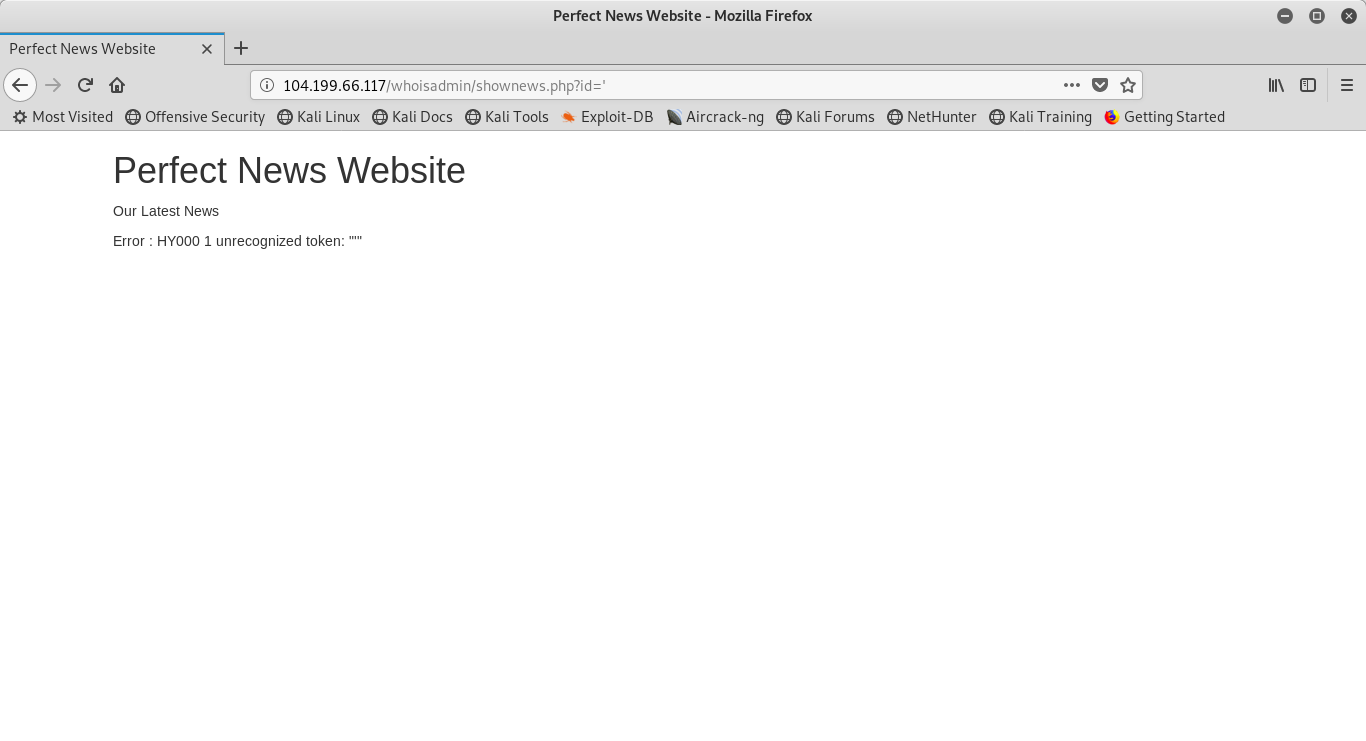
Notice that my url submission is http://104.199.66.117/whoisadmin/shownews.php?id=’ and the output that I am greeted with is Error : HY000 1 unrecognized token: “‘”. While this doesn’t give me a plethora of information about the back end SQL database, it does lead me to believe that it is SQL injectable and that the inputs are not being properly sanitized. For this reason, my next suspicion is to test it in SQLMAP. As a best practice, I always run SQLMAP with the default risk and level, just to quickly see if it looks promising. If it fails the first time, I may increase the level, but in my experience, if it can find a vulnerability that is susceptible to SQL injection, then it will suggest so in the first few seconds at the default levels. After running SQLMAP, this is what was returned:
Since the injectable variable was a web parameter, there was no need to set to –data=’id=’ switch since the variable is being passed in the url and not in the request body. Also, SQLMAP defaults to –method=GET, so there is no need to set that switch here either. As we can see, the output tells us that, on a basic test, it might be injectable, then that indications of database type of H2 (which is wrong, but it later corrects for that); the list goes on. SQLMAP identifies that there are 5 columns and that the back end is SQLite. Finally, it identifies the following output:
I opted to not save the hashes to a file for later cracking, because I knew my objective was to try to identify the email on file as my flag, and I wanted to see SQLMAP dump the table for me to evaluate. As we can see from this table, there are 20 users, one is admin, with an email of ryan@secret.org, and that is our flag.
